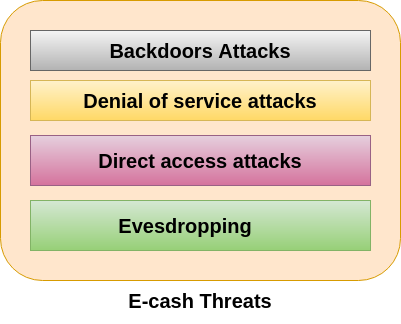
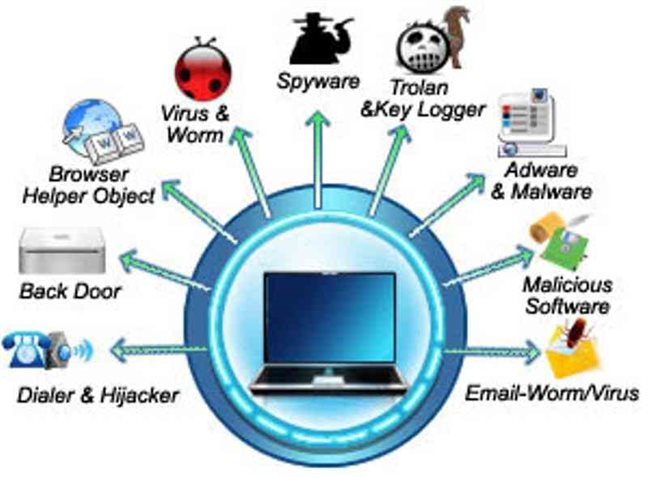
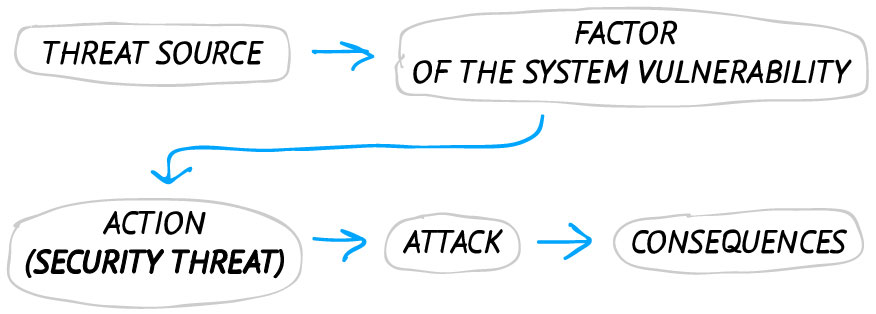
Explain Different Security Threats

The most common network security threats 1.
Explain different security threats. Masters of disguise and manipulation these threats constantly evolve to find new ways to annoy steal and harm. Different types of computer system security threat there are many different types of security threats to computer systems as follows. Disgruntled employees internal attacks are one of the biggest threats facing your data and systems states cortney thompson cto of green house data. Conduct penetration testing by modeling real world threats in order to discover vulnerabilities.
We ve all heard about them and we all have our fears. We ve covered the history of web exploiting and the biggest exploits the world has experienced but today we re going back to basics exploring and explaining the most common network security threats you may encounter while online. Perform regular threat assessments to determine the best approaches to protecting a system against a specific threat along with assessing different types of threats. A computer security threat may cause damage to hardware software data information or processing capability of a computer system.
Types of cybersecurity threats. Virtually every cyber threat falls into one of these three modes. Arm yourself with information and resources to safeguard against complex and growing computer security threats and stay safe online. Sometimes these documents have teeth as in someone s job is on the line.
A combination of several different approaches using a variety of malware elements generating multiple forms of viruses worms and trojan horses. Although the terms security threat security event and security incident are related in the world of cybersecurity these information security threats have different meanings. Threat can be anything that can take advantage of a vulnerability to breach security and negatively alter erase harm object or objects of interest. Security threat short description.
Computer security threats are relentlessly inventive. Cybersecurity threats come in three broad categories of intent.